My attitude about "spoofware" or malware disguised as "helpers".
I yap a lot about music and I haven't talked much about computers lately. They're my second and abiding love behind the exploration of sound and the organization of it that is music. For what is really at the very bedrock of computers and their operations? Numbers. Numbers and the orders of their operations. But this is in the abstract and I am here to talk about something that is just a giant P.I.T.A. (Pain In The Ass)
I am being delicate, because this is the kind of thing that has me foaming at the mouth, not that I am too far from that state of mind generally anyway, but this is something that hits consumers and people who are not all the familiar with two things; one of them being, computers in general, and the other being, the absolutely sordid ways in which people who should know better will take advantage of consumers. The innerwebz is a dangerous place, and just because you're on a safe site doesn't mean you're entirely safe.
I'm an experienced computer user and then some. Beyond then some. I build virtual machines and run Backtrack, which is what hackers work with then they are learning the craft. I am on the fence as far as being a "white" or a "black" hat. Unfortunately, you'll never know until it's too late. I rebuild computer systems from the ground up around here for my neighbors continually, because they blunder onto some idiot site and end up with a spoof screen that threatens them with prosecution from the FBI, and I have a formidable set of tools that allow me to bring their systems back to life. When I worked at IBM, one engineer, in awe at some fix I cobbled up, proclaimed that I "practiced the Dark Arts!" No boast, but I understand computers; the curtains, carpet and furniture (software) may change, but the foundations (logic) remains the same.
That being said and to keep this short, and to illustrate a problem I run into continually, but know how to stop cold, I want to talk about a few things that less-savvy computer users are aware of: spoofing, fraud and "over the transom" malware.
Now, "spoofing" refers to a branding of a product that is not the real thing. It's the cybersphere's definition for counterfeit and in this case, it is Mozilla's Firefox that is being spoofed. For the time being, I am using FF to write my posts, because, Google will not allow my to insert images without using their f'ing Cloud Drive and I have my own back-up, thank you. But that's another story and I want to stay on task.
Today, as I was trying to look at my stats before posting something else, I had written last week, I was "prompted" by Mozilla that my browser was out of date. All well and good. I clicked on the download button and saved the file to my Download folder. I closed my browser and navigated to the folder and saw this:
This is what I would expect to see for a normal Firefox update.
I ran the download through my AVG and Spybot programs before clicking on download, but after clicking on download, this is what I saw:
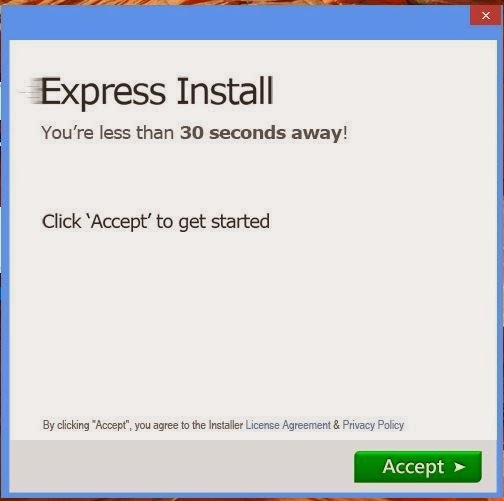
Admittedly, I was suspicious because the UAC (User's Access Control) screen prior was from "Premier Downloads" and not "Mozilla or Firefox". The download is also verified with Verisign™, which speaks badly for them, but I proceeded, knowing what was to come. This screen appeared, with no FF branding, and the screen was very small and hard to read. I clicked "Accept".
Even though Firefox and Search Protect** are mentioned together in the same sentence, this is not an endorsement! Again, the writing and screen are very small. In the lower left-hand corner is the option to install Search and Protect and it's already selected. I de-selected it and clicked "Accept".
Even though Firefox and Search Protect** are mentioned together in the same sentence, this is not an endorsement! Again, the writing and screen are very small. In the lower left-hand corner is the option to install Search and Protect and it's already selected. I de-selected it and clicked "Accept".
I've already pulled up Chrome by this time and am typing in "Search and Protect" in Google. Then, I see this:
**search protect become searchprotect in Google
Now, I have two more search perimeters: "Browser Safeguard**" and "RocketTab". I add these to my Google search and hit "Enter".
I don't have to look any farther than this to know that this is what is known as "malware," and while not necessarily a virus or a trojan, it can hijack your system, or re-direct you to places you do not wish to go. Sites like CleanMyPC.com will advertise as free and then after the first "cleaning" will want money to continue the service. All of this is an unnecessary expense to consumers.
This is where this particular "spoof" originates from. As I said, just because this guy says he is protected by Verisign™ that means nothing, and is no imprimatur of honesty. Once a consumer is caught up into this, they will be hounded into paying, and will continue to get advertisements and unwanted spam. Mozilla is "openware" which means anyone can write apps for it, so if you use it, you have to be very diligent about what you download. However, the honest developers advertise their plug-ins or widgets as such and don't try to disguise their apps as Firefox itself!
There. . . Now it's gone on to Software Heaven!
In Windows 7, you can right-click on the icon > Properties > General. Here is where I found that the program is "blocked". Which means nothing to Windows, because. . . Microsoft. Microsoft doesn't even see the spoof as it tells us this is "Firefox_Setup". Microsoft is like your elderly aunt who warned you not to drive all over town without gasoline, because she didn't understand how cars worked. I rest my case.
**browser safeguard becomes browsersafeguard in Google
I don't have to look any farther than this to know that this is what is known as "malware," and while not necessarily a virus or a trojan, it can hijack your system, or re-direct you to places you do not wish to go. Sites like CleanMyPC.com will advertise as free and then after the first "cleaning" will want money to continue the service. All of this is an unnecessary expense to consumers.
This is where this particular "spoof" originates from. As I said, just because this guy says he is protected by Verisign™ that means nothing, and is no imprimatur of honesty. Once a consumer is caught up into this, they will be hounded into paying, and will continue to get advertisements and unwanted spam. Mozilla is "openware" which means anyone can write apps for it, so if you use it, you have to be very diligent about what you download. However, the honest developers advertise their plug-ins or widgets as such and don't try to disguise their apps as Firefox itself!
Here are a few key things to follow when downloading any updates, whether for drivers, browsers, JAVA (which should be abandoned ASAP, it is unnecessary and is a horrible place! Known for bugs. It is what we termed a "bug-patch," or "bug-farm" at IBM and Verizon, more and more HTML5 apps are coming out. JAVA is strictly for Apple and was never meant for PC and DOS-based systems) and even operating systems, as Windows updates are not always necessarily. Remember, Windows and Microsoft lies!
- 1. Save the file you are downloading.
- 2. Before running the install, close all programs that are running, including your browsers.
- 3. Scan the downloaded file, preferably with something like AVG and either malwarebytes and/or Spybot. One scans for viruses, the other scans heuristically, for trojans. NOTE: They will NOT tell you that a download is MALWARE necessarily! You have to use your judgment, after this!
- 4. If you DO NOT see an authentic branding for the product itself, halt the installation immediately and delete the setup.exe file from your Download folder.
In Windows 7, you can right-click on the icon > Properties > General. Here is where I found that the program is "blocked". Which means nothing to Windows, because. . . Microsoft. Microsoft doesn't even see the spoof as it tells us this is "Firefox_Setup". Microsoft is like your elderly aunt who warned you not to drive all over town without gasoline, because she didn't understand how cars worked. I rest my case.
I already know this is at best a headache; but at worst? This can cripple a system and force a rebuild. I make no apologies for the fact that I live in a low-income neighborhood, but if it's a dangerous neighborhood, it's also a neighborhood full of proud grandmas and grandpas who have oodles of pictures of their grand kids saved to their desk tops. To our credit, my partner in this little enterprise and I have yet to lose a single precious moment.
But this today, is a special kind of forgery, a spoof. I suspect this cat could be shut down easily and arrested, for he is not only spoofing, but blatantly using Firefox's brand to mask his malware and that's fraud. I've run these things down, but since the FBI doesn't have me on the payroll, let them pursue it and since I'm so damn lazy, I'm not even filling out reports anymore; I just send them links. I am just doing my bit to let my readers know that all of this is out there and you need to be damn careful. Next week, I think I'm going to put out some tutorials for maintaining your PCs, and laptops, Windows only, to start.
I don't do anything with Apple products and thus have no use for JAVA. I keep my phones, Kindles and mobile stuff completely separate from my home devices, but that is okay, I'm pretty much a shut-in, anyway, and there is no need for me to synchronize stuff. At this juncture, iPads, iPods and PCs really don't mix. I hope Microsoft wakes up and dumps the Surface. Now, I'm editorializing.
As a side note, and a bit of hilarity, while I was pulling together the information for this post, I ran across an old nemesis, BrokenControllers.com. A while back, they stole a post of mine, "Playing the Violin, and How to Avoid It," and sold it on their website. I was alerted to this by another blogging buddy, of which I have legions! This is rather ironic and to me pretty funny, since I've never earned a penny for my writing. Enjoy my take on the violin, but take my advice on downloading anything, even from a supposed trusted sight to heart!









4 comments:
You're a woman of many talents, Mary :) You're way ahead of me when it comes to computer savvy, plus I use a Mac, which is way simpler to handle, even down in the entrails/code level. This post resonated with me because I deleted the Java plug-in a couple of weeks ago (with Flash who needs it?) and, by mistake, deleted a bunch of Java-related but not dangerous files that kinda made my OS crash :D So I spent a couple days rebuilding it... I'm a big backuper, so not much in the loss of files, but it was still a PITA (*love* that!) :D
@Guilie,
I'm a woman of exactly two talents and I pretend to know the others! But thank you for the kind words. I do NOT play the violin, although I have sto- uh, earned many dollars doing so.
MAC systems are entirely foreign to me. When I went back to school to major in computer science because I was stupid enough to marry another violist (we met playing the "Nutcracker" in Detroit), who I fear, labored under the delusion that the Zither Fairy would wave magic dust over me and Presto! no more competition, we studied DOS-based systems and the attendant math and logic.
The first time I was presented with a MAC was when I worked at IBM and we had exactly one for about 20 engineers, but we had "shells" that worked much like virtual machines do now and allowed us to fix MAC-related problems. I however, felt as if I were a cow, being presented with a steering wheel and decided to stick with what I knew.
The end result of this was me hollering to a MAC user who was just a little more out-of-it than I was (in 1997) to a floor of 100 engineers "A box? A BOX IS A THING SHAPED LIKE A SQUARE!!" in an attempt to fix an MS WORD 6.0 problem for Macs, which was a horrible, horrible legacy program.
I, at that point, sealed my legendary status and moved on to OS/2, about which I knew even less, but it was a great floor show! Until I learned the system, and then I ruled, seriously.
PITA is for the more sensitive among us, because I can be SOOO salty and I wish to at least attempt to fit in. People have this idea that musicians are these hot-house flowers, when in reality, we're more like a group of sailors on shore-leave.
I'm so happy you solved your issue! Macs ARE awesome! I feel that we stick with what we initially learn, and I started out with the architecture and the mathematics of the PCs and command line programming. I've seen people do similar things with MACs, but I am a stranger in a strange land! My hats off to you, Guilie! xoxo Mary!
Very informative post. Thank you so much for sharing all this detailed information.
MJ, A to Z Challenge Co-Host
Writing Tips
Effectively Human
Lots of Crochet Stitches
@M.J.
Thanks for stopping by! Every so often, I get on a kick when I run into some particularly, sophisticated and nasty thing that is aimed at consumers who really don't have the time and energy to be that aware. Nor should they be and until these kinds of scams and spoofs are stopped, people will lose money and precious data.
I appreciate your kind comments. I rove back and forth, from the musical world to the computer world; thank you so much for visiting! Mary
Post a Comment